Cloud ComputingTechnology Law / Cyber Law
Cloud Computing

WHAT IS CLOUD COMPUTING?
It provides a platform to access data or program over the internet or has that data synced with other information over the web. It impacts an individual’s consumers and business entities. It requires the data to be sent over the internet and stored on a third-party system.
CLOUD COMPUTING IN BUSINESS ENVIRONMENT
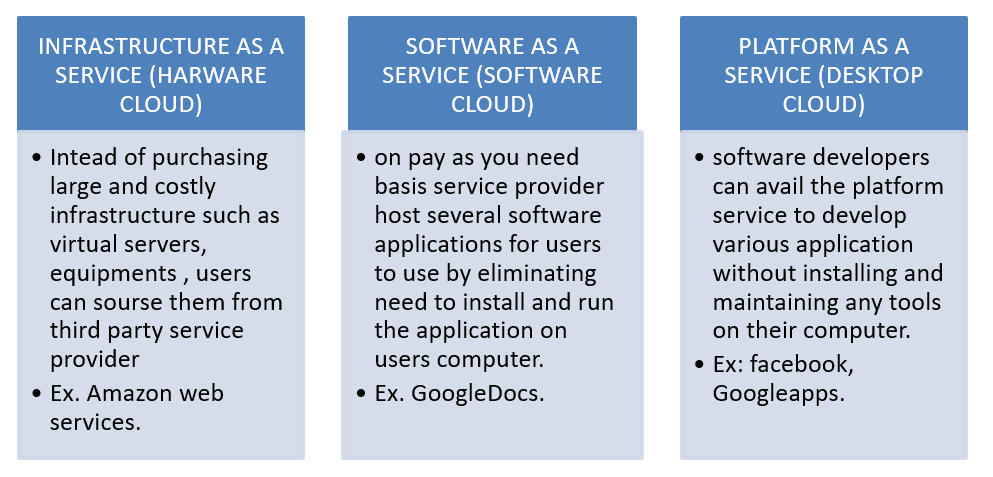
As there are three layering models:-
- Client or customer
- Cloud service provider
- Cloud host company
The customer to solve its business computing problems on the pay per use basis use the services provided by a cloud service provider with the help of intermediatory i.e. cloud Host company.
Cloud computing is a business method where dynamic IT capabilities such as hardware, software, and tools are provided by third parties or cloud service providers which enables the users to store as well as access their data and application virtually from anywhere and through any connected device.[1]
If the servers are used for data storage the third party doesn’t have any right to tamper/modify the contents of the data where customer having its own application entered into a contract with the vendor to store data electronically and that vendor stores data on third party network.
PRIVACY UNDER CLOUD COMPUTING
Management and privacy of data play key role in the adoption of cloud computing. IT Act, 2000 puts certain restriction on the organization to store personal data. Such as section 43A and 79 of the IT Act are directly associated with cloud computing. To protect private and sensitive data, notification was issued by the central government where “Reasonable security practices and procedures and sensitive personal data or information Rules, 2011” are made in compliance with section 43A. These Rules prescribed guidelines for the collection, usage, and protection of sensitive personal data or information of natural persons.[2]
SECTION 43A of IT ACT, 2008
It provides for compensation for negligence in implementing and maintaining reasonable security practices and procedures in relation to sensitive personal data or information.
Under Section 43A of the Information Technology Act, 2000, a body corporate who is possessing, dealing or handling any sensitive personal data or information, if it is negligent in implementing and maintaining reasonable security practices resulting in wrongful loss or wrongful gain to any person, then such body corporate will be held liable to pay damages to the person so affected. There is no upper limit specified for the compensation that can be claimed by the affected party in such circumstances.
RESONABLE SECURITY PRACTICES AND PROCEDURES AND SENSITIVE PERSONAL DATA OR INFORMATION RULES, 2011
| (1) | Password |
| (2) | Financial information such as bank a/c or credit card or debit card or other payment instruments details |
| (3) | Physical, physiological and mental health conditions |
| (4) | Sexual orientation |
| (5) | Medical records and history |
| (6) | Biometric information |
| (7) | Any detail relating to the above clauses as provided to body corporate for providing service and |
| (8) | Any of the information received under the above clauses by the body corporate for processing, stored or processed under lawful contract or otherwise |
RULE 3: Definition: sensitive personal data
Exception: Information available in public domain or furnished under the right to information Act, 2005 or any other law, for the time being, will not be considered as personal information or sensitive personal information.
This article is first of the series on Cloud Computing.
Stay connected for more! LinkedIn Facebook
[1] Barnaby page,’Cloud computing a guide for business managers’ available at: www.icaew.com/-/…management/cloud-computing-a-guide-for-business-managers.ashx
[2] Cloud computing risk challenges- legal and tax issues, march 2013. Available at: www.nishithdesai.com/fileadmin/user_upload/pdfs/Cloud_Computing.pdf
This article has been contributed by our Advisory Board member Mr. Rodney D. Ryder.




